![Group_26843[1] Group_26843[1]](https://nextgen.group/hubfs/Group_26843%5B1%5D.png)
Security and Compliance
AWS Best Practice Report
Cloud computing providers present a large, robust offering with a seemingly infinite number of configuration options to tailor your deployment perfectly around your needs. However, the flexibility and sheer number of choices that a cloud provider offers when setting up your services are both a blessing and a curse. It can be easy to overlook security loopholes, deploy options that aren't the most cost-effective, or miss beneficial features that are hidden within the API.
.png)
Our application takes a detailed look at your deployment to ensure your infrastructure is configured properly, and highlight areas that may be cause for concern. These checks will focus on four key areas: security, availability, cost, and usage.
While your cloud computing provider handles security of their data center, users are responsible for network, host, and application-level security. CloudCheckr will look and see if you are setting proper permissions, if security groups are being utilized properly, if access and permission controls are configured correctly, if proper password policies are in place, if resources are accessible by the public internet, and several other items.
When items are launched in your deployment, it's important that they are accessible. However, sometimes things can go wrong, such as instances becoming unhealthy or certain data centers becoming unreachable. CloudCheckr will look at your deployment to not only verify that everything is up and running, but also ensure that your architecture is properly configured to respond when things do go awry.
When launching and maintaining an infrastructure, it's easy to lose track of what's out there and what's no longer needed. CloudCheckr can help with this. We will look for items that exists but aren't being used, and highlight those for you. Cost checks will also show you potential cost savings by making RI purchases, optimizing your subscriptions, or leveraging any available discounts, as well as migrating resources to current generation offering types.
There are many options within a cloud environment that, though highly recommended, may not be consistently or properly deployed. CloudCheckr will review your architecture to see whether you are taking advantage of these features, and whether they are being used in the most advantageous way. We will ensure that autoscaling is configured, and configured properly, within your servers. We'll ensure that the users in your identity management portals are created according to best practices. That backups are taken automatically and retained for an appropriate amount of time. And that resources are being properly utilized.
If customers use AWS Trusted Advisor and have provided CloudCheckr with access to this feature, the application can import the results into the AWS Trusted Advisor tab in the report.
.png?width=1600&height=786&name=unnamed%20(8).png)
To provide CloudCheckr with access to Trusted Advisor, customers must allow "support:*" permissions on the IAM user used in CloudCheckr. Submit a ticket to Support via the CloudCheckr Service Desk Portal if you have any questions.
The top section of the report allows you to filter your checks by:
- Category
- Importance
- Tag
- Ignored Checks
- History
.png?width=1600&height=219&name=unnamed%20(9).png)
The table references each callout in the screenshot.
| Callout | Name | To Filter |
| 1 | Importance | Select All, High, Medium, Low, Informational, or Ok from the Importance drop-down menu. |
| 2 | Tag | Select a resource tag associated with your account from the Tag drop-down menu. |
| 3 | Show Ignored | Select or deselect the Show Ignored check box to view or restore those items that you have flagged to ignore. |
| 4 | Tab | Click one of the report tabs: Availability, Cost, Security, Usage, or Trusted Advisor. |
| 5 | History | Select a day from the History drop-down menu and filter for the specific date. |
After you have made your selections, click Filter to apply your changes to the report.
The items in the report are also categorized by icons and colors.
| Color | Icon | Description | Example |
| Red | -png-1.png) |
High |
-png.png) |
| Orange | -png-1.png) |
Medium | -png.png) |
| Yellow | -png.png) |
Low | -png.png) |
| Blue | -png.png) |
Informational | -png.png) |
| Green | -png.png) |
No issues found | -png.png) |
The report lists the name of each best practice check and the number of items that CloudCheckr identified which meet the criteria for the best practice check.
-png.png)
If only one item meets the criteria for the best practice check, no number will be displayed.
If no items meet the criteria for the best practice check and the check passes, the bpc will be displayed in green with a checkmark.
-png.png)
To view the details for a Best Practice Check, click the name.
The Best Practice Check expands and identifies the items in your deployment that met the requirements for the selected best practice check.
-png.png)
The table references each callout in the screenshot.
|
Callout |
Name |
Description |
|
1 |
Summary |
Describes what the BPC looked for in your deployment. |
|
2 |
Read more |
Contains more detail about the check results. See Read More section for more information. |
|
3 |
Link |
Redirects you to the details report for the selected item. A View All... link redirects you to the details report for all items. |
|
4 |
30-Day Trend Graph |
Shows how many items were found for a specific check each day within the last 30 days. If you see any spikes or anomalies that you want to investigate, select a date from the History drop-down menu to filter the report by the selected date. |
When you click Read More, you will see the following details:
-png.png)
The table references each callout in the screenshot.
|
Callout |
Name |
Description |
|
1 |
Category |
Describes the type of best practice check: availability, cost, security, or usage. |
|
2 |
Importance |
Identifies the level of importance: high, medium, low, or informational. |
|
3 |
Description |
Provides an overview of the feature that the best practice check was run against, why the check is important, and how it impacts an account. |
|
4 |
Link |
Links to the relevant AWS documentation. |
|
5 |
Recommendation/Remediation |
Tells you how to prevent a potential adverse condition or how to fix a current adverse condition. |
To the right of each check, you will find several icons. The number and type of icons depends on the selected check.
The table identifies each icon and the action(s) that you can perform with it.
|
Icon |
Name/Tooltip |
Purpose |
|
|
Export |
Export details of the selected check to comma-separated value (CSV) file. |
|
|
Notifications |
Create email notifications that selected users will receive when new issues are discovered or configure to have emails sent daily regardless of any changes. See the Configure Best Practice Check Notification topic for more information. |
|
|
Notify of New Issues |
Send email notifications to selected users will receive when new issues with an ignored check are discovered. |
|
|
Ignore Check |
Hides checks that are irrelevant to your deployment. Also, the application will not send ignored checks in any email notifications. |
|
|
Restore Check |
Restores the check that you had selected to ignore. |
|
|
Edit Ignore Reason |
Modify the reason why you are ignoring a check. |
|
|
Configure |
Modify the parameters that trigger a check. For example, you can dictate the CPU Utilization % and Time Period that determines when an EC2 instance will be considered idle. |
|
|
Tags |
Configure the check to only report on resources that have specific resource tags.
|
If you ignore an item, as opposed to a check, the check will still show up in your report and email, but the individual item(s) you have ignored will be hidden.
-png.png)
This functionality is also available on the individual items found within each check. If you expand a check, you can click the Hide icon to the right of the item to ignore that specific item while leaving the main best practice check active.
Security: Configuring AWS Config Alerts
CloudCheckr's Alert Builder ensures that CloudCheckr alerts you when specific conditions within your AWS deployment are met.
CloudCheckr allows you to create an unlimited number of alerts across multiple alert types. You can base alerts on costs, resource usage (such as EC2, or S3), or AWS activity recorded by the CloudTrail and/or AWS Config services.
To build an alert based on changes detected from AWS Config:
- Choose the Resource Changes (via AWS Config) alert type from the drop-down menu. The Alert Builder page opens—giving you AWS Config-specific options.
- Type a name for your alert. CloudCheckr will use this name in the subject line of the alert emails you receive.
Alert Delivery Options
After you create your alert, you can choose how you want CloudCheckr to deliver your alerts:
- Email: email address(es) where you want to send the alert; separate multiple addresses with a comma
- SNS Topic: ARN value of an SNS topic
The IAM user whose credentials were added to CloudCheckr needs sns:Publish permissions to use this feature. - PagerDuty: your PagerDuty service API key, which will route the alert through PagerDuty's alerting system
Alert Parameters
After you create your alert, you can choose how you want CloudCheckr to deliver your alerts:
- Resource Deleted
- Security Group Modified
- All Security-Related Changes
When you select one or more of these options, you refine the selected resource type and/or change type for the alert. For example, selecting Security Group Modified allows the alert builder to filter the Resource Type by EC2 Security Group.
You can further refine your configurations by the following parameters:
- Availability Zone: the location of the resources that will trigger the alert
Not all resources are tied to an availability zone.
- Resource Type: the type of resource, such as EC2 instance, Security Group, or VPC Subnet
- Change Type: the type of change that you want to trigger an alert such as Resource Deleted, Relationship Created, and Tag Modified
You can choose one, all, or any combination of these parameters.
You can also select Build your own filter from below to configure your own filters.
You can also choose to filter your alert by specific resource ID or by resource tag.
Adding CloudCheckr as a Subscriber to Your Config SNS Topic
For AWS Config alerts to function successfully, you must add CloudCheckr as a subscriber to your AWS Config SNS topic. This action allows CloudCheckr to process the SNS notifications to ensure the alerts are triggered in real-time, instead of waiting for CloudCheckr to retrieve the log files from S3.
To add CloudCheckr as a subscriber of your SNS topic:
- Copy the Endpoint URL from the Alert Builder.
- Log into the SNS Service within the AWS Management Console.
- Locate and select the SNS Topic used for AWS Config from the list of topics.
- Click the Create New Subscription button.
- In the dialog box, paste the Endpoint URL into the associated text field.
- For the Protocol option, verify that you selected HTTPS.
- Click Subscribe.
CloudCheckr will automatically confirm the subscription and your AWS Config alerts can now be delivered.
CloudTrail Alerts
CloudTrail alerts are notifications that will help you to secure your cloud deployment. You can use these alerts to get notified about any of our out-of-the-box security issues, or you can create your own customized alerts. The results of the alerts are communicated to you and are also saved within CloudCheckr, providing you with a starting point to conduct audits and perform forensics on your deployment.
How Do I Use CloudTrail Alerts?
A good starting point is the built-in alerts. CloudCheckr has developed ready-to-use alerts to help you stay on top of security-related issues in your deployment. This topic will show how to configure a built-in alert.
From the left navigation pane, choose Security > Alerts > CloudTrail > Manager.

Built-In Alerts
The Alert Manager has two tabs: Built-In Alerts and Custom Alerts. For this exercise, let's start with the default setting, Built-in Alerts.
.png?width=1175&height=277&name=unnamed%20(1).png)
Click the title of any built-in alert to review the details. In this example, we clicked Any security-related event.
.png?width=1168&height=141&name=unnamed%20(3).png)
The first section shows in the alert name, risk level, and custom description field.
.png?width=1169&height=86&name=unnamed%20(4).png)
Notifications
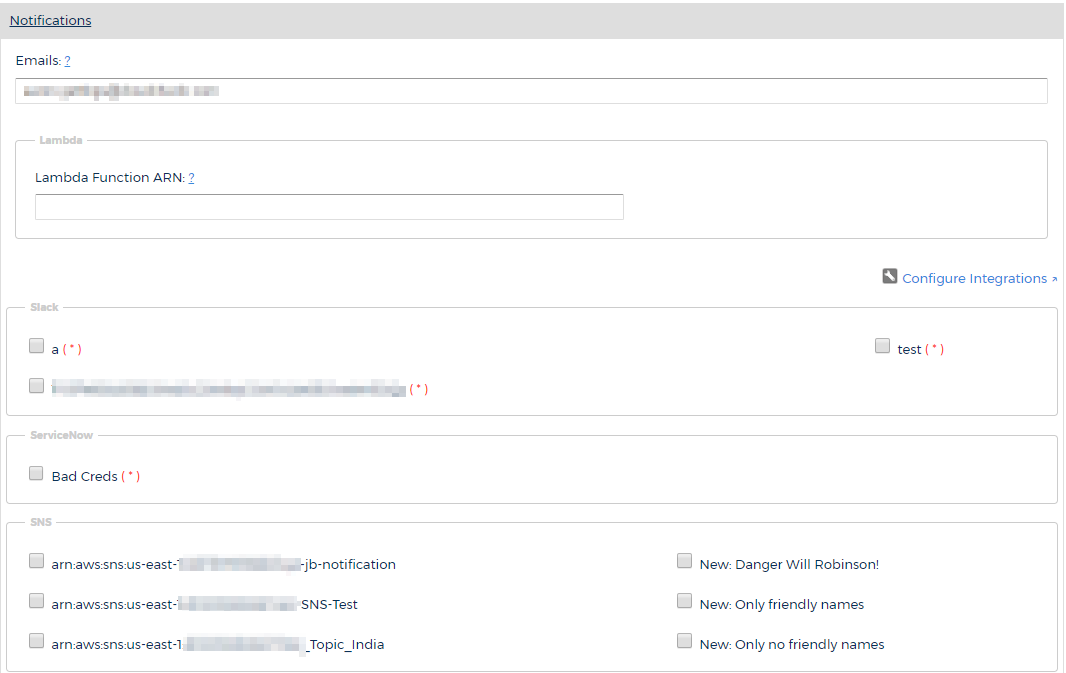
Click Notifications to expand this section.
The Notifications section allows you to configure how you want CloudCheckr to notify you about alerts. You can select one or more of the following notification options:
- Email: email address(es) where you want CloudCheckr to send the alert email
- Lambda: AWS Lambda function that you want CloudCheckr to call to perform a specified action
- Slack: prompts CloudCheckr to push the alerts to a Slack channel via a webhook
- SNS: prompts CloudCheckr to push the alerts to SNS
- PagerDuty: prompts CloudCheckr to push alerts via the PagerDuty API
- Syslog: communicates information, such as Security Information and Event Management systems (SIEM), and other information
Click Filters to expand this section.
The Filters section allows you to refine your search by the following parameters: region, service, event, and user.
Each drop-down menu is populated with search criteria for the selected parameter.
To get more information on the search criteria, click (Binoculars) next to the associated parameter.
The screenshot shows the filters you can select for the Events parameter for the built-in alert, Any security-related alert.

Advanced Options
Click Advanced Options to expand this section.
The Advanced Options section allows you to determine how CloudCheckr responds to CloudTrail events.
-1.png?width=1194&height=586&name=unnamed%20(8)-1.png)
Here are the available options:
Event Filters
- Response Type: the type of event that the alert will respond to. For built-in alerts, the default response type is All and you cannot change it. For custom alerts, however, the alert can look for Success, Failure, or Unauthorized Access.
- Resource ID: the type of resource that you want the alert to respond to. For built-in alerts, you cannot edit this field.
Threshold to fire
By default, this section is blank, so the alert will trigger or fire every single time that CloudTrail encounters a matching event. Since a cloud deployment often contains many AWS API calls, this default setting could result in a large number of alerts. To reduce the number alerts, you can customize the threshold. For example, you might tell CloudTrail to only fire when 20 matching events occur within a one-minute time period.
Request & Response
A CloudTrail event is going to have a Request parameter and a Response parameter. You can customize the alert so that it only fires if the selected parameters are or are not present in the event data.
IP Address Filters
You can restrict the IP address range that the alerts monitor—effectively doing things such as white-listing your own address range or making sure that the alerts do not alert on IP addresses originating from AWS.
Misc
By default, CloudCheckr saves the results of your CloudTrail alerts, but you can turn off this functionality and just use the selected notification method (email, Slack, etc.).
Ignored
Click Ignored to expand this section.
The Ignored section displays all the alert results that you have ignored.
-1.png?width=1075&height=129&name=unnamed%20(9)-1.png)
If you want to ignore selected CloudTrail Alert results, go to the left navigation pane and choose Security > Alerts > CloudTrail > Results. On this page, you will see all of your results and can select which results you want to ignore.

The Ignore Configuration dialog box for the selected alert will display.

Your configuration shows you the parameters that you can select to ignore for the selected alert.
You can also choose to ignore an alert from the alert notification email.
After you have configured the alert results that you want to ignore, CloudCheckr will list them in the Ignored section.

Custom Alerts
Custom alerts function in the same way as the Built-In alerts.
To create a custom alert, go to the Alert Manager page of CloudTrail and click + New Alert or click Copy Alert in a selected built-in alert.
The Create New Alert dialog box opens.
.png?width=1057&height=429&name=unnamed%20(10).png)
Type a name for your custom alert and configure the other parameters identified in the Built-In Alert section.
If you copied an existing built-in alert, CloudCheckr will pre-populate the search criteria. If your custom alert is not based on a built-in alert, you will need to select your search criteria. Click the Alert me when I see... drop-down menu to use the options from the built-in alert as template for your custom alert.
Once you have configured your custom alert, save it and make sure that you turn on the alert by moving the slider ON.
.png?width=1050&height=93&name=unnamed%20(11).png)
Alert Results
CloudCheckr will send your CloudTrail alerts in the notification format and parameters that you configured in the Built-in and Custom Alerts tab, such as email, Slack, or SNS. CloudCheckr also provides you with a comprehensive and searchable list of all your alert results. To get your results, go to the left navigation pane, and choose Security > Alerts > CloudTrail > Results.
The Alert Results page contains the details about your alerts: what event triggered the alert, when the alert occurred, where the alert occurred geographically, and who triggered the alert.
Click the (green plus icon) to expand the results of the alert including the raw JSON content for the event that triggered the alert.
.png?width=1037&height=338&name=unnamed%20(14).png)
Sending CloudTrail Alerts to Lambda Functions
The CloudTrail Alert Manager allows you to enable or disable CloudCheckr's built-in or custom CloudTrail alerts. When AWS CloudTrail detects specific events, it triggers a CloudTrail alert.
CloudCheckr can notify customers about these alerts by email, SNS, Pager Duty, Syslog, Slack, or Lambda function.
This topic focuses on how to configure a notification via a Lambda function.
What is the Lambda Function?
Lambda is an AWS service that allows its users to upload code, and runs the code on their users. To get the service to execute your code, you must create a Lambda function, which consists of code and any associated dependencies. When Lambda executes a function on your behalf, it takes care of provisioning and managing the resources needed to run the function.
When you configure your CloudTrail alert in CloudCheckr, your must enter the Lambda function ARN value. When the alert is triggered, CloudCheckr will send the full event JSON file (plus other useful properties) as a payload to the Lamdba function. This action will invoke the Lamdba function, allowing you to automate activity within your Amazon account based on CloudTrail alerts.
For this functionality to work, you must update the IAM policy associated with your account credentials with lambda:InvokeFunction permissions. It is recommended that you qualify the permission with the name of the function. Without this permission, CloudCheckr will not be able to invoke the function on your behalf.
Obtaining the Function ARN
To obtain your function's ARN value, launch your AWS Management Console, open the Lambda service, and select the function with the ARN value you would like to use.
You will see your ARN value displayed in the top-right corner of the console. Copy the ARN value, so you can add it to the CloudTrail alert in CloudCheckr.
.png?width=996&height=454&name=unnamed%20(15).png)
Adding ARN to CloudCheckr Alert
To update the alert(s) where you want to invoke your Lambda function:
- Launch CloudCheckr, and open the account that contains the CloudTrail alert that you want to update.
- From the left navigation pane, choose Security > Alerts > CloudTrail > Manager. On this page, you will see the Built-In and Custom tabs for the CloudTrail alerts. You can configure any of these alerts with your Lambda ARN.
- Click the name of the alert that you want to update. For the purposes of this procedure, we selected the built-in alert, Any security-related event. CloudCheckr displays details about the alert.
.png?width=947&height=254&name=unnamed%20(16).png)
- Click Notification and in the Lambda Function ARN text field, type the ARN value.
.png?width=949&height=290&name=unnamed%20(17).png)
The next time the alert is triggered by CloudCheckr, the payload will be delivered to the Lambda function.
How To Set Up Resource Alerts in CloudCheckr
Resource alerts allow you to monitor, manage, and act on any resource changes that occur in your cloud deployment.
You can configure CloudCheckr to send you an email any time it discovers:
- a new publicly accessible resource
- changes to your AWS Config setup
- changes to your security groups
CloudCheckr considers it a best practice to set up a resource alert for any new publicly accessible resources.
Resource alerts allow you to review these changes and make informed decisions on how they could impact your deployment.
This topic will show you how to set up an alert and where to find your alert results.
Procedure
Imagine a CloudCheckr customer who has expanded their global footprint by acquiring several new offices in the UK and in Europe. As a result, the customer's IT department will have to purchase more resources to successfully handle the changes to the cloud infrastructure.
In this procedure, we will set up a resource alert that will notify the customer when there is a new publicly accessible resource.
- Launch CloudCheckr.
- Select the account where you need to set up the resource alert.
- From the left navigation pane, choose Security > Alerts > Resources > Manager.
- On the Alert Manager page, click + New Alert.
- From the Type drop-down menu, select the condition that will trigger an alert.
- Type a name for your alert.
- Under Frequency, leave the default setting to send an email alert daily or select the Only send once checkbox.
- Under Notifications, select the resources that apply in this alert.
- Click Create alert.
Here is an example of what the screen would look like if our fictitious customer created a resource alert that will notify them when CloudCheckr discovers a new publicly accessible EC2 instance:
.png?width=988&height=618&name=unnamed%20(18).png)
In addition to the email notification, you can navigate to Security > Alerts > Resources > Results to view your alert results.
CloudCheckr Alerts
CloudCheckr can alert when any number of critical events occurs within your AWS account. These alerts, which can be delivered via email, SNS topic, or PagerDuty, are also logged within your CloudCheckr account to be reviewed at any time.
With CloudCheckr you can be alerted when you approach your monthly budget, when someone accesses your account using the Root user account, when a publicly accessible resource is launched, plus several other important scenarios. These alerts can be found within their own section of the report navigation within each account. From there you can choose to manage Cost, Utilization, and CloudTrail alerts.
Within each section you'll find an Alert Manager, where you can create/modify/delete your alerts, and an Alert Results page where you can track your triggered alerts.
Create Cost Alerts
- Go to the left navigation pane and choose Cost > Alerts > Manager. The Alert Manager page will open.
- Click the New Alert button. The Cost Alert Builder opens.
The Cost Alert Builder allows you to create user-defined alerts based on a defined billing budget.
.png?width=964&height=576&name=unnamed%20(19).png)
Create Utilization Alert
- Go to the left navigation pane and choose Utilization > Alerts > Manager. The Alert Manager page will open.
- Click the New Alert button. The Utilization Alert Builder allows you to create alerts to monitor the utilization of your resources.
.png?width=970&height=589&name=unnamed%20(20).png)
You can choose from the following types of utilization alerts:
- EC2 Number of Instances: the number of EC2 instances running in your AWS account.
- EC2 Resource Utilization: the average CPU for the last 24 hours of any instances in your AWS account.
- New Publicly Accessible Resources: the availability of new public resources within the last 48 hours.
- Reserved Instance Utilization: notifies you if a reserved instance is under or unutilized.
- Resource Changes (via Config): shows you any changes in resources based on your AWS config data.
- S3 Storage Used: the total S3 storage across all of your buckets.
- S3 Total Objects: the total number of S3 objects stored across all of your buckets.
In addition, you can configure how you want to be notified (email, SNS, PagerDuty, etc.)
Explore the Alert Manager
The Alert Manager is where you can view and manage all of your created accounts.
.png?width=641&height=153&name=unnamed%20(22).png)
You can take the following actions on any alert:
- Delete: click X to the far right of the alert to delete it.
This cannot be undone. (Arati could we put this in an orange box like the blue box) - Disable: click On to the right of the alert to disable it. No alerts will be triggered on disabled alerts. They can be re-enabled at any time by clicking Off.
- Edit: click the name of any alert that you would like to edit and modify any configuration options as needed.
Alert Results
In addition to the notification sent when an alert is triggered, the details of the alert will be saved on the Alerts results page. You can filter this page by the alert type, the specific alert name, as well as the start and/or end date of the alert.
.png?width=1258&height=76&name=unnamed%20(4).png)
CloudTrail Alerts
To access and create a CloudTrail alert:
- Go to the left navigation pane and choose Security > Alerts > CloudTrail > Manager.
The Alert Manager page will open. - Click the New Alert button. The CloudTrail Alert Builder opens. The CloudTrail Alerts section focuses on security alerts. They use CloudTrail data from your account. To use these alerts, you must have CloudTrail enabled on your account and CloudTrail permissions must be added to your permissions policy. Although similar to other alerts, CloudTrail alerts also include uniquie features such as pre-configured alerts.
CloudTrail Alert Manager – Built-In Alerts
The CloudTrail Alert Manager allows you to enable/disable CloudCheckr’s recommended pre-configured Built-In CloudTrail alerts, or manage your custom alerts. Within the Built-In Alerts tab, you enable or disable the pre-configured alerts. You can click any alerts to see specific events and parameters that will trigger the alert, as well as configure the notification method. The Built-In Alerts allow you to quickly enable alerts without having to scour through the list of events to find the correct event types for your alert.
.png?width=1024&height=450&name=unnamed%20(25).png)
CloudTrail Alert Manager – Custom Alerts
The CloudTrail Custom Alert Builder allows you to create alerts based on all available events that are logged by the AWS CloudTrail service, including resource creation and deletion, modifications to IAM policies, and VPC reconfigurations. You can copy any pre-existing Built-In alert and modify its parameters, or you can click the Create New Alert button to create an alert from scratch. hen creating CloudTrail alerts you can filter the alerts by events coming from specific AWS regions, services, or from specific IAM users. You can also only be alerted to events that occur within (or outside) of specific IP ranges, that occur against specific resources, or that contain specific Response and/or Request parameters. This gives you flexibility to be alerted to the precise activity that's important to you. You also have the ability to ignore specific results to eliminate any noise, and review those ignored items later if necessary.
CloudTrail Alert Results
In addition to the notification sent when an Alert is triggered, the details of the Alert will be saved within the CloudTrail Alert Results page of your CloudCheckr account. This report offers several filtering options and the ability to choose which columns to show in the results. You can expand any alert to see further details, including the raw JSON of the CloudTrail event that triggered the alert. You also have the ability to ignore individual results.
.png?width=1024&height=478&name=unnamed%20(26).png)
Compliance
Total Compliance
The Total Compliance feature reviews more than 30 compliance frameworks against the configuration of AWS accounts and resources.
By leveraging the Total Compliance standards, security professionals can more easily and consistently ensure that their deployments are following established best practices for compliance.
To access the Total Compliance page, go to the left navigation pane, and choose Compliance > Total Compliance.
.png?width=1027&height=559&name=unnamed%20(27).png)
CloudCheckr updates the data weekly and the results are stored for multiple months.
By default, the Total Compliance page shows weekly results. Select Show Daily View at the top of the page to allow CloudCheckr to pull daily results. Choosing the Daily View may increase the time it takes to load the report.
Functionality Overview
The Total Compliance page lists each control and its state of compliance. To get more information, click a selected control. In this example, we chose the control, AICPA SOC2 and SOC3 TSPC.
.png?width=1023&height=419&name=unnamed%20(28).png)
CloudCheckr uses its Best Practice Checks as a source of data for each of the controls. Click
(green plus sign) to see details on the Best Practice checks associated with that control, its status (Correctly or Not Correctly Set), and any remediation comments.
.png?width=1023&height=351&name=unnamed%20(29).png)
Features
The table describes each of the features on the Total Compliance page.
|
Feature |
Example |
Description |
|
Control |
Control 1.1 - Avoid the use of the “root” account |
Name and description of a control in the AWS CIS Foundation report. |
|
Plus icon |
|
Click to show the details about the selected control. |
|
Minus icon |
|
Click to hide the details about the selected control. |
|
Best Practice Check |
|
The name of the Best Practice Check associated with the selected control. The color and icon of the check indicates if it is passing or failing for your deployment. Clicking the name of the check takes you to the location and details in the Best Practice report. |
|
Remediation Comment |
Add a remediation comment |
Text field where you can insert a message about remediation. |
|
Submit button |
|
Click Submit to add the remediation comment. |
|
Set Correctly |
|
Indicates if the the control is configured correctly for the selected deployment. |
|
Favorites |
|
Click the Click the |
Total Compliance Standards and Regulations
Here is a list of the Total Compliance Standards and Regulations that CloudCheckr adheres to and monitors in your cloud deployment:
|
Standard |
Industry |
Geo |
Description/Use Case |
|
AICPA GAPP |
Accounting |
US |
The American Institute of CPAs’ Generally Accepted Accounting Principles (GAAP) are uniform minimum standards of, and guidelines to, financial accounting and reporting. See the AICPA website for details. |
|
AICPA SOC2, SOC3 TSPC |
Accounting |
US |
The International Auditing and Assurance Standards Board (IAASB) ensures security, availability, and privacy of computing operations. See the IAASB and AICPA websites for details. |
|
ANSSI - 40 Measures |
Universal |
Global |
The French Network and Information Security Agency (ANSSI) standard addresses computer security including user authentication, networking, upgrades, monitoring, and incident response. See the ANSSI website for details. |
|
Australian Essential 8 |
Universal |
Australia |
Australia’s recommendations to avoid Malware, limit intrusions, and improve availability. See the Essential Eight Explained page for details. |
|
Australian Top 35 |
Universal |
Australia |
More extensive strategies from Australian Signals Directorate covering access, privilege, Multi-Factor Authentication (MFA), auditing, updates, firewalls, filtering, password policy, and more. See the Strategies to Mitigate Cyber Security Incidents page for details. |
|
Center for Internet Security |
Universal |
Global |
The Center for Internet Security (CIS) is a non-profit organization that includes industry experts and delivers a cybersecurity framework independent of any government or industry. See the CIS Controls page for details. |
|
COBIT 5 / SOX |
Accounting |
US |
COBIT is a widely-accepted formal set of compliance requirements to meet the 2002 Sarbanes-Oxley Act, which regulates external audits and financial reporting. See the ISACA COBIT and Sarbanes-Oxley Act pages for details. |
|
CoM 201 CMR 17.00 |
Universal |
Massachusetts |
In 2017, the Commonwealth of Massachusetts established these protections for Massachusetts residents regarding privacy, breaches, encryption, and monitoring. See the 201 CMR 17.00 regulation for details. |
|
CSA CCM v3 |
Cloud |
Global |
The Cloud Security Alliance (CSA) has developed cloud-computing-specific best practices. While many other regulations were designed for the data center, pre-Cloud, and need to be “translated” to cloud technology, the CSA is cloud-first. See the Cloud Controls Matrix publication for details. |
|
DHS CDM Program |
Government |
US |
The Department of Homeland Security (DHS) has a scorecard for monitoring, diagnostics, and mitigation. See the DHS/CISA/PIA-030 Continuous Diagnostics and Mitigation (CDM) page for details. |
|
FFIEC Booklet 2016 |
Financial |
US |
The Federal Financial Institutions Examinations Council (FFIEC) created a booklet in 2016 that addresses Risk (identification, measurement, mitigation, monitoring, and reporting.) See the FFIEC Information Technology Examination Handbook for details. |
|
FFIEC CAT |
Financial |
US |
The Federal Financial Institutions Examinations Council (FFIEC) has a Cybersecurity Assessment Tool that works as a scorecard for specific metrics related to the FFIEC Booklet. See the FFIEC Cybersecurity Assessment Tool document for details. |
|
FY15 FISMA Metrics |
Government |
US |
The 2002 Federal Information Security Management Act/Electronic Government Act (FISMA) protects government IT against man-made and natural threats. See the Federal Information Security Modernization Act page for details. |
|
HIPAA |
Healthcare |
US |
The 1996 Health Insurance Portability and Accountability Act (HIPPA) mandates privacy and portability of health records. See the HHS Health Information Privacy page for details. |
|
IEC 62443-3-3-2013 |
Universal |
Global |
The International Society of Automation (ISA) and the International Electrotechnical Commission(IEC) developed standards for security vulnerabilities, risks, and security levels and is approved by the United Nations. See the United Nations commission to integrate ISA/IEC 62443 into Cybersecurity Regulatory Framework article for details. |
|
IRS Pub 1075 |
Government |
US |
The Internal Revenue Service (IRS) has guidelines for protecting tax information such as returns that include Personally Identifiable Information like Social Security Numbers (SSNs), bank account numbers, and more. See Publication 1075 for details. |
|
ISO 27002-2013 |
Universal |
Global |
The International Standards Organization (ISO) has guidelines regarding security controls and management, assessment, contractors and providers, and information handling. See the ISO/IEC 27002:2013 page for details. |
|
ITIL 2011 KPIs |
Universal |
Global |
ITIL (originally an acronym for Information Technology Infrastructure Library) describes processes, procedures, tasks, and checklists that are neither organization-specific nor technology-specific, but can be applied by an organization toward strategy, delivering value, and maintaining a minimum level of competency. It allows the organization to establish a baseline from which it can plan, implement, and measure. It is used to demonstrate compliance and to measure improvement. Individuals, but not organizations, can be certified via training. See the What is ITIL? page for details. |
|
NERC CI v5, v6, v7 |
Energy |
US |
North American Electric Reliability Corporation (NERC) is for power plants and the Critical Infrastructure Protection (CIP) standards evaluate and ensure compliance with reliability standards, pursuant to the Federal Power Act. See the NERC Compliance & Enforcement page for details. |
|
NIST 800-171 |
Government |
US |
National Institute of Standards and Technology (NIST) 800-171 corresponds to Defense Federal Acquisition Regulation Supplement (DFARS), which is designed to keep federal systems secure but is also relevant to organizations that have access to federal data, such as financial aid information. See the Archived NIST Technical Series Publication for details. |
|
NIST 800-53 rev4 |
Government |
US |
National Institute of Standards and Technology (NIST) 800-53 is the basis for the Federal Risk and Authorization Management Program (FedRAMP) that agencies often must abide by when selecting vendors. See the FedRAMP website for details. |
|
NIST 800-82 rev2 |
Government |
US |
This standard from the National Institute of Standards and Technology (NIST) deals with security architecture, firewalls, traffic, access, audits, and planning. See the Guide to Industrial Control Systems (ICS) Security for details. |
|
NIST Cybersecurity Framework |
Universal |
US |
The National Institute of Standards and Technology (NIST) Cybersecurity Framework is focused on business practices and activities (identify, protect, detect, respond, recover) more than technology. See the NIST Cybersecurity Framework for details. |
|
NIST SMB Guide |
Small/Mid-size Business |
US |
National Institute of Standards and Technology (NIST) has resources based on their Cybersecurity Framework, specifically focused on small and medium-sized businesses. See the Small Business Cybersecurity Corner page for details. |
|
NSA MNT (MNP) |
Government |
US |
The National Security Agency (NSA) has a framework to take an unmanageable, insecure network and make it more defensible, secure, and manageable. See the Manageable Network Plan (MNP) Guide for details. |
|
NSA Top 10 |
Government |
US |
The National Security Agency (NSA) publishes a Top Ten Cybersecurity Mitigation Strategies that covers updates, accounts, policies, recovery, and management. See the NSA’s Top Ten Mitigation Strategies document for details. |
|
NV Gaming MICS |
Gaming |
Nevada |
The Nevada Gaming Commission has their own security controls with specific requirements for different types of gambling. See the Minimum Internal Control Standards (MICS) document for details. |
|
NYCRR 500 |
Financial |
New York State |
New York State has established regulations—with penalties—for financial entities that don’t follow their rules for audits, access, application security, personnel, third parties, Multi-Factor Authentication (MFA), data retention, training, and monitoring. See the Adoption of New 23 NYCRR 500 document for details. |
|
PCI DSS 3.2 |
Financial |
Global |
The Payment Card Industry Data Security Standard (PCI DSS) is an industry standard that regulates credit card companies and related firms. See the PCI Document Library for details. |
|
Saudi AMA |
Financial |
Saudi Arabia |
The Saudi Arabian Monetary Authority (AMA) released their Cyber Security Framework in 2017 that covers policy, roles, risk management, and even compliance with other standards. See the Cyber Security Framework document for details. |
|
SEC OCIE Audit Guide for AWS |
Financial |
US |
The U.S. Securities and Exchange Commission (SEC) Office of Compliance Inspections and Examinations (OCIE) is responsible for protecting investors, ensuring market integrity, and establishing guidelines for risk management. They have mapped these guidelines specifically to Amazon Web Services (AWS). |
|
SG MAS TRM |
Financial |
Singapore |
The Monetary Authority of Singapore (MAS) has established guidelines on risk management with specific sections on cloud computing. See the Guidelines on Risk Management Practices for details. |
|
Victorian PDSF v1.0 |
Universal |
Australia |
The State of Victoria, Australia has created guidelines specifically related to cloud computing. See the Victorian Government Cloud Security Guidance page for details. |
CIS Benchmark
Tell The Reader More
The CIS Benchmark page provides guidelines on how to configure security options for a range of AWS services.
By leveraging the standards articulated in the CIS Benchmark for AWS, security professionals can more easily and consistently ensure that their deployments follow established best practices for compliance.
For more details on how our Benchmark feature can help you meet CIS requirements, review The Best Security Tools for Cybersecurity in the Cloud article.
Summary
Go to the left navigation pane and choose Total Compliance > CIS Benchmark to access this feature.
.png?width=1023&height=436&name=unnamed%20(30).png)
Each control and its state of compliance is listed clearly. CloudCheckr uses its Best Practice Checks as a source of data for each of the controls.
Each control is categorized under one of the following areas of compliance: Identity and Access Management, Logging, Monitoring, or Networking.
.png?width=1023&height=431&name=unnamed%20(31).png)
Click the Expand button to see details on the Best Practice checks associated with that control, whether it is scored (Automated) or not (Manual), its status (Correctly or Not Correctly Set), and any remediation comments.
.png?width=1023&height=436&name=unnamed%20(32).png)
Features
The table describes each of the features on the CIS Benchmark page.
|
Feature |
Example |
Description |
|
Level 1 and Level 2 tabs |
|
Level 1 and Level 2 are security configuration profiles.
|
|
Category |
|
Each control is grouped under one of the following categories:
|
|
Control |
|
Name and description of a control in the AWS CIS Foundation report. |
|
Plus icon |
|
Click to show the details about the selected control. |
|
Minus icon |
|
Click to hide the details about the selected control. |
|
Best Practice Check |
|
The name of the Best Practice Check associated with the selected control. The color and icon of the check indicates if it is passing or failing for your deployment. Clicking the name of the check takes you to the location and details in the Best Practice report. |
|
Remediation Comment |
|
Allows you to insert a message about remediation. |
|
Submit button |
|
Click Submit to add the remediation comment. |
|
Set Correctly |
|
Indicates if the control is configured correctly for the selected deployment. |
|
Scoring |
|
Indicates if the control is scored (Automated) or not (Manual). |
|
Slider |
|
Allows you to toggle Yes or No to indicate if the condition is met (manual attestation). |
HOW DID WE DO?
Contact The Nextgen Marketing Hub and tell us what you need.
We willl take care of the rest.
![Group_26888[1] Group_26888[1]](https://nextgen.group/hubfs/Group_26888%5B1%5D.png)